PowerShell - Get/Set the Network Level Authentication Remotely (RDP Setting)
![]() A few days ago I was in a training class out of the office with one of my work colleague. During the class he tried to connect to work using our Citrix (SRA) portal when he realized that his computer at work (freshly re-installed with Windows 8.1) was not allowing him to connect because of the Network Level Authentication.
A few days ago I was in a training class out of the office with one of my work colleague. During the class he tried to connect to work using our Citrix (SRA) portal when he realized that his computer at work (freshly re-installed with Windows 8.1) was not allowing him to connect because of the Network Level Authentication.
Error message:The remote computer that you are trying to connect to requires Network Level Authentication (NLA), but your Windows domain controller cannot be contacted to perform NLA. If you are an administrator on the remote computer, you can disable NLA by using the options on the Remote tab of the System Properties dialog box.”
/NLA__1667311512__-583x182.png) Before I talk about the workaround and the PowerShell script we used to fix that, let’s investigate in order to understand the problem.
Before I talk about the workaround and the PowerShell script we used to fix that, let’s investigate in order to understand the problem.
What is Network Level Authentication ?
Network Level Authentication is a technology used in Remote Desktop Services (RDP Server) or Remote Desktop Connection (RDP Client) that requires the connecting user to authenticate themselves before a session is established with the server.
Originally, if you opened a RDP (remote desktop) session to a server it would load the login screen from the server for you. NLA delegates the user’s credentials from the client through a client side Security Support Provider and prompts the user to authenticate before establishing a session on the server. This is a more secure authentication method that can help protect the remote computer from malicious users and malicious software.
Network Level Authentication was introduced in RDP 6.0 and supported initially in Windows Vista. It uses the new Security Support Provider, CredSSP, which is available through SSPI since Windows Vista.
The advantages of Network Level Authentication are:
- It requires fewer remote computer resources initially. The remote computer uses a limited number of resources before authenticating the user, rather than starting a full remote desktop connection as in previous versions.
- It can help provide better security by reducing the risk of denial-of-service attacks.
Requirements of Network Level Authentication
- The client computer must be using at least Remote Desktop Connection 6.0.
- The client computer must be using an operating system, such as Windows 8.1, Windows 8, Windows 7, Windows Vista, or Windows XP with Service Pack 3, that supports the Credential Security Support Provider (CredSSP) protocol.
- The Remote Desktop Session Host “server” must be running
- Windows Client: Vista or newer (Vista, 7, 8, 8.1)
- Windows Server: 2008 R1 or newer (2008R1, 2008R2, W2012R1, W2012R2)
Workaround using the UI
Go to Control Panel / System and Security / System and select Remote Settings

In the Remote tab, in the remote Remote Desktop group you will have to uncheck “Allow remote connections only from computers running Remote Desktop with Network Level Authentication (recommended)”
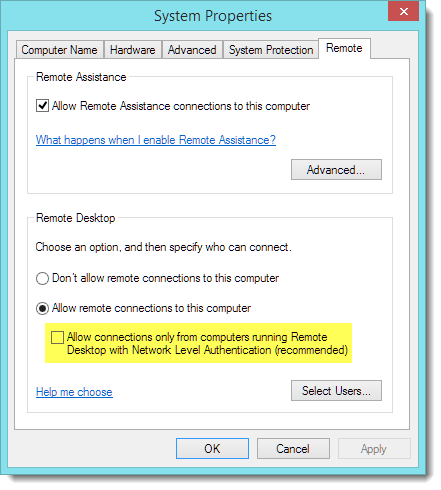 |
| Windows 8/8.1/2012 Remote tab |
 |
| Windows Vista/7/2008 Remote Tab |
The user will then be able to connect to the server or workstation.
Using PowerShell One-Liners
We used the classWin32_TSGeneralSettingto get the information of the current NLA setting.
Quick answer, you can do this using the following commands:
$ComputerName = "SERVER01"
# Getting the NLA information
(Get-WmiObject -class "Win32_TSGeneralSetting" -Namespace root\cimv2\terminalservices -ComputerName $ComputerName -Filter "TerminalName='RDP-tcp'").UserAuthenticationRequired
# Setting the NLA information to Disabled
(Get-WmiObject -class "Win32_TSGeneralSetting" -Namespace root\cimv2\terminalservices -ComputerName $ComputerName -Filter "TerminalName='RDP-tcp'").SetUserAuthenticationRequired(0)
# Setting the NLA information to Enabled
(Get-WmiObject -class "Win32_TSGeneralSetting" -Namespace root\cimv2\terminalservices -ComputerName $ComputerName -Filter "TerminalName='RDP-tcp'").SetUserAuthenticationRequired(1)
Using PowerShell Advanced Functions (re-usable tools)
I created two re-usable advanced functions for this purpose
- Get-NetworkLevelAuthentication
- Set-NetworkLevelAuthentication
You can download those from the Technet Gallery.
Running the functions
First import the functions using the Dot Sourcing method
. .\Get-Set-NetworkLevelAuthentication.ps1
Use the function Get-NetworkLevelAuthentication to retrieve the current setting.
Get-NetworkLevelAuthentication
Use the function Set-NetworkLevelAuthentication to change the NLA setting
Set-NetworkLevelAuthentication -EnableNLA $true
 Use the function Get-NetworkLevelAuthentication with a list of computers:
Use the function Get-NetworkLevelAuthentication with a list of computers:
Get-NetworkLevelAuthentication -ComputerName (Get-Content -Path d:\ServersList.txt)
Building the functions
First we investigate the class Win32_TsGeneralSetting using the cmdlet Get-WMIObject. The property UserAuthenticationRequired is the value that control the NLA setting.
Get-WmiObject -Class Win32_TSGeneralSetting -Namespace root\cimv2\terminalservices
Finding the methods We can retrieve the methods available using Get-Member.Here we are interested at the method SetUserAuthenticationRequired.
Get-WmiObject -Class Win32_TSGeneralSetting -Namespace root\cimv2\terminalservices | Get-Member -Type Methods
Using CIM cmdlets However in my functions I decided to use CIM Cmdlets, you can retrieve the same information using the following:
Get-Ciminstance -Class Win32_TSGeneralSetting -Namespace root\cimv2\terminalservices
However when you check the methods, you will notice the same methods are not available.
Get-Ciminstance -Class Win32_TSGeneralSetting -Namespace root\cimv2\terminalservices | Get-Member -Type Method
Find CIM Methods Cim Cmdlets don’t work the same way, we need to use Get-CimClass cmdlets instead with the property cimclassmethods.
(Get-Cimclass -Class Win32_TSGeneralSetting -Namespace root\cimv2\terminalservices).cimclassmethods
Invoking CIM Method We use the cmdlet Invoke-CimMethod to call this method. With this method you need to pass the arguments using a hash table.
Invoke-CimMethod -MethodName SetUserAuthenticationRequired -Arguments @{ UserAuthenticationRequired = $EnableNLA }
The MSDN page of this method show us how to use it:
Download
- Technet Repository
- Github - Get-NetworkLevelAuthentication
- Github - Set-NetworkLevelAuthentication
/NLA_RDP_Supported__1565359304__-346x226.png)
/2014-04-02_21-44-36__2015979677__-692x778.png)
/2014-04-02_21-47-35__1889517893__-692x330.png)
/2014-04-02_21-50-18__1509479296__-692x570.png)
/2014-04-02_21-51-55__664197085__-692x410.png)
/2014-04-02_22-09-37__1699464907__-692x442.png)
/2014-04-04_20-01-37__238174237__-970x905.png)
Leave a comment